1's and 0's Flying Through the Air
Understanding the Internet
Osher Lifelong Learning
Institute
University of Illinois, Urbana-Champaign
Scott Badman, Instructor
Session 3: Internet Security (Part 1)
October 22,
2014
Topics
Fundamentals
Internet Threats and Security
(Another attempt at) The Process of Creating and Posting a Web Page on a Web Site.
Changing the local development copy, and then uploading a modified web page to www.scottbadman.com
Discussion of the Poodle Vulnerability
Are you vulnerable?
How to protect yourself on various browsers.
Port Numbers
Ports are how a single computer with a single IP address can have multiple connections to other computers at the same time.
For example, each web page tab you have open in your browser to different web sites is assigned a different port number.
Ports are 65,355 virtual connections that can be made to each IP address.
They don't actually exist on a computer except as a number inside the operating system.
Ports are maintained by Layer 4, the Transmission Control Protocol (TCP) layer of the ISO-OSI Model (International Standards Organization - Open Systems Interface).
The TCP Layer is a software part of the operating system that maintains multiple end-to-end connections to other computers.
The TCP Layer, as well as all ISO-OSI Model Layers, work the same on all operating systems that connect to the Internet. That is why any computer can connect to any other computer, tablet, or smart phone (or X-Box or web-aware refrigerator for that matter) whatever the operating system.
Some of the lower number Ports are reserved for specific uses.
Port 7 responds to "ping" requests.
Ports 25 and 110 are reserved for use by your e-mail program.
Port 37 will tell you the time, if you have a program that requests it from a Time Server.
Port 53 is used to find out the IP address number when you type in something like www.nytimes.com
The IP address is supplied by a Domain Name Server (DNS) computer.
Port 80 is always used to make the first request for a web page from a web site server computer.
When you type in the "www" at the beginning of a web site name, this really means to the computer "use Port 80".
Even if you don't type in the "www", Port 80 is usually assumed. Try typing in just "nytimes.com" instead of "www.nytimes.com". It still works.
After the first request both computers agree to continue communication using some random high port numbers, in the tens of thousands range up to about 65,000.
Your web browser can maintain multiple web pages at the same time because the communication with each different web site uses a different high port number.
Port 443 is used for the secure https protocol.
Port 546 is used by your computer to get its IP address when it boots up, without you having to enter the number (which you had to do back in the '70's).
Malware
Types of Malware
Malware is any software that does harm to a computer or its user.
Virus
A "virus" is a program fragment that installs itself inside another complete program and reproduces itself by installing a copy of itself into other complete programs on other computers when possible.
Worm
A "worm" is a complete program that makes a copy of itself and installs itself on another computer when possible.
Most Malware today, however, does not try to replicate itself. It gets on your computer by some method in the next section, and simply gathers data, or affects your computer in some way.
Such Malware can be a computer code fragment inside a legitimate program (essentially a virus), a "service" or "deamon" attached to your operating system always running in the background, a corrupted device driver, an extension to your Internet browser, or a stand alone program.
Delivery of Malware
Trojan Horse
Any attractive, seemingly benign program or download that contains malware inside, which is activated when you run the program.
Scareware and Ransomware
Programs, web-pages, e-mails, or pop-ups that try to scare you or otherwise force you to download and run them.
Phishing
A program, web-page, e-mail, or pop-up that tries to trick you into giving personal information.
Commercial web pages from any company, as well as their e-mails, can be convincingly faked. Always go directly to the company's web site.
Microsoft Internet Explorer
Internet Explorer is particularly vulnerable because if its close integration with the Windows operating system.
The other Internet browsers don't have the same vulnerabilities because they are just an application program like any other as far as Windows is concerned.
If you use Internet Explorer, make sure you install all of Microsoft's updates as soon as they are offered.
Microsoft Office Documents
Microsoft Office must access your computer's resources, and has more access to Windows than similar third party programs.
Opening an Office document from an unknown or suspicious source can deliver Malware to your computer.
Don't do that.
If you use Microsoft Office, make sure you install all of Microsoft's updates and also read and think carefully about your answer when Windows presents you with an "User Account Control" pop-up window.
Microsoft Office for MacIntosh has some (but not all) of the same vulnerabilities, and is one of the few sources of Malware problems for the MacIntosh. Be sure you pay attention to MacIntosh's "User Account Control" pop-up windows.
What Malware Does
Direct harm to your computer or data.
This is rare, mainly because there is no profit to be made. Mainly the work of teenage boys, unless some government is interested in you.
Spyware
Collects information about you, usually your browsing habits, but also information about your computer, and sends that information to some computer.
One of the worst Spyware programs is a "Keyboard Logger", which records every keystroke you make, including passwords and financial information. This technique bypasses all encryption techniques.
Zombie Computers and Botnets
Sometimes the writer of Malware is not interested in you, but just wants to use your computer to do other (usually illegal) things.
Malware installed on your computer can run in the background without your knowledge and perform services that you would not want done, such as launder money or attack other computers.
Some Malware "entrepreneurs" have access to large numbers of such "Zombie Computers", called "Botnets" (short for RoBOT NETworks), which they rent to various nefarious "businessmen".
Denial of Service Attack
Overwhelming a target web server with a huge number of data requests, so the web server must shut down.
Usually done with Botnets of unknowing Zombie Computers.
Social Engineering
Almost all successful attacks involve tricking a human in some way.
In one good study, leaving a flash drive on the ground in a government parking lot, with an official seal on it, resulted in 90% of the government employees picking up the flash drive and plugging it into their computer to see what was there.
Any request for passwords or financial information, unless you specifically went to the site by typing it into the browser's address window, is highly suspicious.
Running any program or clicking on any link or inserting any drive, unless you know and trust the source, is very dangerous.
Other Vulnerabilities
Interception of your data when using Wi-Fi
Anyone with a computer can intercept your data when broadcast using Wi-Fi, and read it if it is not encrypted.
Man-in-the-Middle attack
If a hacker can place his computer in the middle of any electronic communication, he can do a number of nefarious things.
He can just passively collect the data as it streams through his computer for use later, without either end knowing that anything is happening.
He can change the data as it goes through to suit his purposes, also without either end knowing that anything is happening.
He can pretend to be one side of the exchange in such a way that the other side never knows the difference. The computer that he is pretending to be will have no record of the transaction.
He can use his position in the middle of the stream to set up other kinds of attacks, such as downloading malware.
He can alter the communication stream, such as slowing it down, so that both sides think something else is happening.
Hacking into your computer, and more important, your router.
Normally an external hacker can only see your router, but if they can hack into your router then they can see and connect to all the computers in your house.
They can also set up the router so they can intercept everything that goes through it.
Every hacker knows the default administrative username and password for all the brands of routers.
Change it!
Password Cracking
Done with password cracking programs, not a human being sitting at a computer.
Some have 500,000 of the most commonly used passwords in their dictionary, including almost all single English words.
(10 to 15 Minute Break)
Practical Tips and Techniques
How Do I Protect Myself?
Diversion Effect
You don't have to have perfect security, just better security than other, easier targets.
You don't have to run faster than the bear, just faster than the person behind you.
Passwords
Create a good password system.
Don't ever write down your password, anywhere. Instead create an mental system of how you generate a password. Then you can write down a veiled and vague description of that system -- just enough so you'll remember the whole process, but not enough that someone can recreate the password just from the description of how it was created.
Have multiple levels of passwords.
One for almost "public use" for when some website or program demands a password, but you don't intend on using it very much and it would not be serious if someone cracks the password.
One for medium level security, such as stores or credit card accounts, where the damage a hacker can do is relatively limited.
One for extremely limited use for your very important financial information, such as investments, where the damage would be very great.
Requirements for a really secure password
At least 12 characters, 16 or 20 is much better.
Use of almost all the various categories of characters that print on the screen - both lower and upper case, digits, and symbols.
Stay away from any English words, unless significantly changed by some kind of character substitution.
Stay away from anything common or obvious, such as easily obtained public information about yourself, common phrases, and obvious patterns of characters.
Best system I've heard of:
Pick something memorable in your personal history that involves the alphabet that almost no one knows about, such as an event, a favorite saying, or a newspaper headline.
Pick something memorable in your personal history that involves numbers, such as an old address, a date, or an old phone number.
Combine them in systematic, but non-obvious way, throwing in punctuation or symbols in some memorable way.
Don't write down the password, but you can write down cryptic hints, that only have meaning for you, about how you created that password.
Change your password on a regular basis -- quarterly or semi-annually is probably O.K. for personal, non-commercial use.
In your mental system of how to create a password, have a place for something that changes, in a significant way with a not-easily-guessed manner of changing.
For instance, multiply the year by the quarter (2014 times the 4th quarter would be 8056) and then insert the day of the month of your birthday, mulitplied by the quarter (for me 23 time 4 or 92, into the middle of the year result. For me that would be 809256. I would make that the numeric part of my passwords.
This solves the problem of having to remember constantly changing passwords. If you forget to change one of your many password accounts, you can just go backwards from the current password until you hit the old one that was the last one you used at that web site.
Password Management Programs
Without a doubt the most secure system - they create long, totally random passwords from all the characters of the keyboard.
However, you still have to remember a "master password", which, if it ever compromised or lost, means you can lose all your security and access.
Apple has a somewhat complicated, but excellent, master password program called "Key Chain" built into the operating systems. Windows has no equivalent.
Put a strong password on all User accounts on your computer, especially the administrative accounts.
Home Routers
Use a home Router with your Internet connections at home, even if you only have one computer.
A Router uses the Internet address your Internet Service Provider, such as Comcast, gives you, and gives a special "internal address" to your computer. This essentially disconnects your computer from the Internet, with the Router taking over responsibility for allowing traffic through. All common brands of home routers have very tight security built in.
Normally adding a home router won't give a home user any problems, but you may have to change some of the settings in the router if you set up something such as home security cameras.
Properly set up your home Wireless Router
Put a strong password on your home router's administrative account.
Turn on your Wi-Fi's WPA2 security, with a strong password.
This requires that you use the same password on your computer when you connect to the Wi-Fi.
Typical (in this case a Netgear brand) Wireless Router Menu System
as a Power Point presentation (very large file)
as a .pdf file (loads faster)
Connecting to an unsecured Wireless Hot Spot at a public place
In Windows, Always, always, always designate your network as "Public" when you make a connection outside your home (i.e. not behind your Router), such as at Panera Bread or a motel.
Normally you will be given this choice when you first connect to a wireless network. Always choose "Public" unless you are at home behind a wireless router connection.
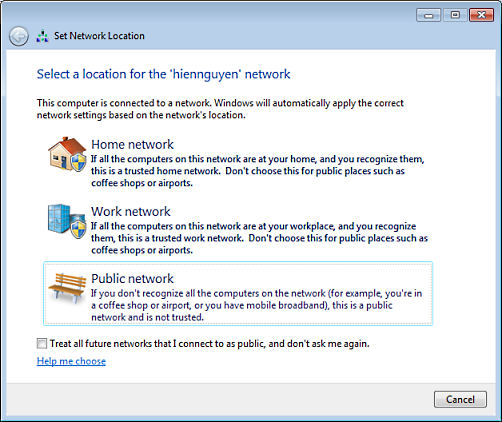
Mac OS / X does not have the equivalent of this security feature.
Turn off the automatic wireless login feature of your portable computer and mobile devices (but not on your home Wi-Fi if you are using a good Wi-Fi WPA2 password.)
This means, however, you will always have to manually connect to the public network every time you use it.
One trick is for hackers to offer their computer as obvious unsecured log-ins, such as "Panara", and see what computers connect to them.
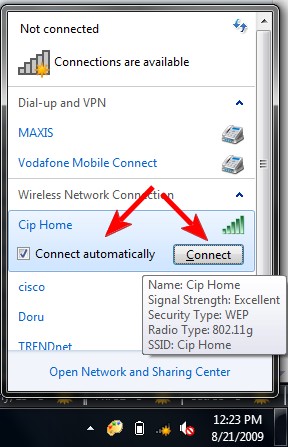
Normally you will be given the choice of remembering a wireless network when you first connect to a new wireless network. Always choose "No" unless you are at home behind a wireless router connection.
Windows: uncheck Connect automatically before you press Connect
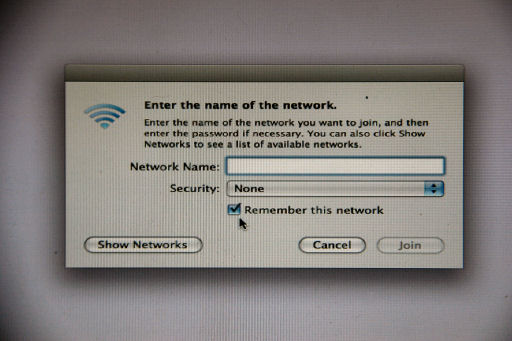
Mac: uncheck Remember this network before you press Join
Operating System Considerations (surprisingly consistant no matter which operating system you are using)
Always keep your operating system up to date.
Windows Update is turned on by default when Windows is installed. Don't turn it off. It updates Windows, Microsoft Office and all other Microsoft applications or Apps. Accept all "Critical Updates". The other updates are optional.
Windows: Start - Control Panel - System and Security - Windows Update - Change Settings
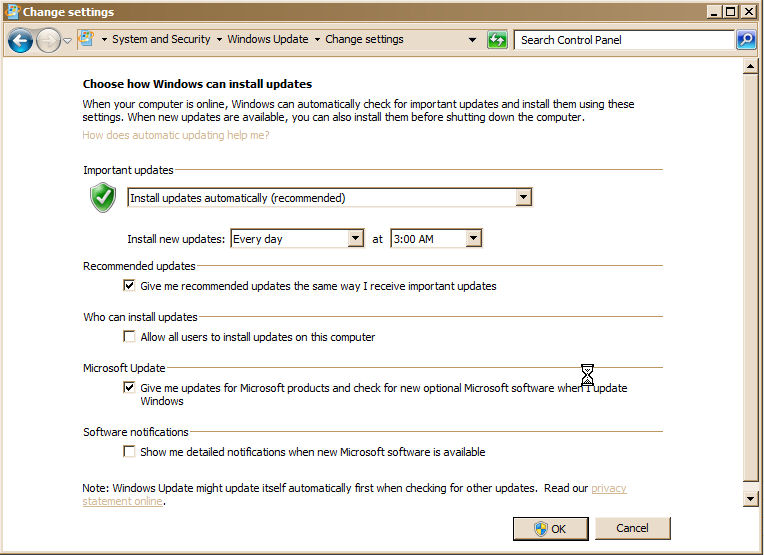
Mac: Apple symbol (upper left corner) - System Preferences - Software Update and make sure that Download important updates automatically is checked.
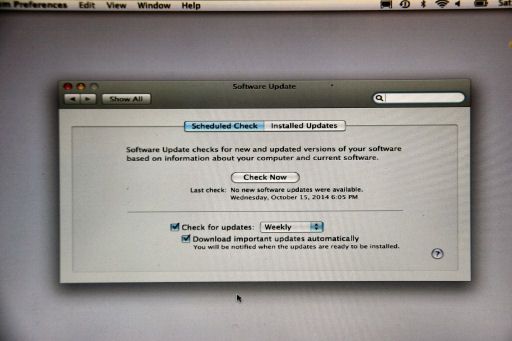
All Apple operating systems update themselves automatically. If asked (which will probably not happen) just accept all updates that Apple offers.
Updates from third party software vendors are more of a problem. Sometimes they actually hinder the operation of the program, or add features you don't want or remove features that you like. Most of their updates are not related to security. Read what they say carefully, and if in doubt, don't update. If it ain't broke...
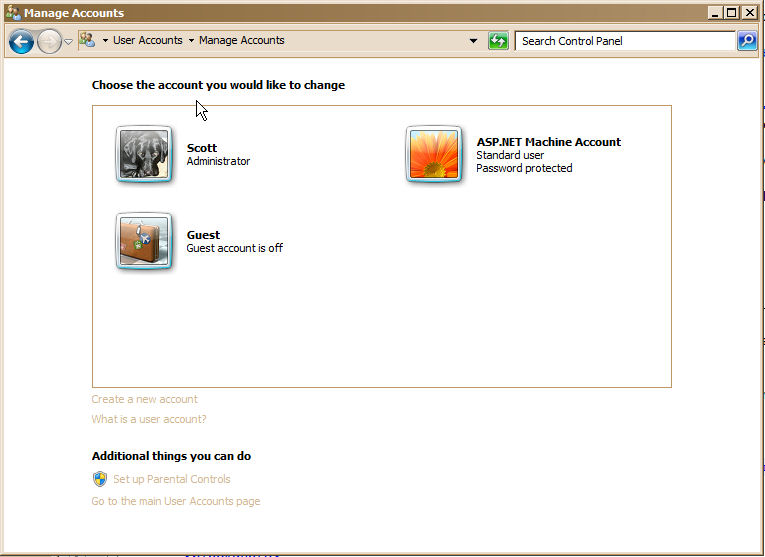
Create a standard User account (without administrative rights) and use that for all your computing.
This gives an extra level of safety to User Account Control.
Windows: Start - Control Panel - User Accounts and Family Safety - Add or remove user accounts - Create a new account
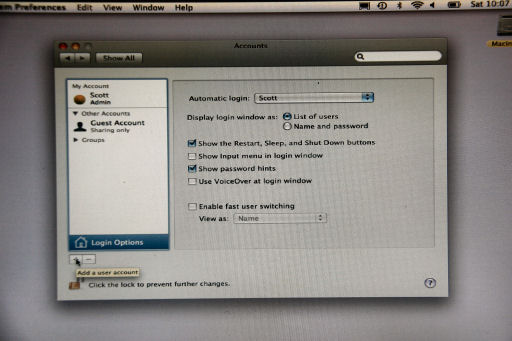
Mac: Apple symbol (upper left corner) - System Preferences - Accounts - Plus (+) button in lower left to add an account.
Leave User Account Control turned on.
User Account Control is responsible for those (sometimes annoying) pop-up menu's from the operating system requiring an administrative password to make any changes to your computer.
They prevent any changes to your computer unless you are aware of them and explicitly give permission.
Since User Account Control is one of the most important ways to prevent what could be extensive harm to your computer, just put up with the annoyance and think carefully when one of the menus appears whether you trust everything that is happening just then.
User Account Control is so important that all the major operating systems, Windows, Mac OS / X, Linux, iOS for iPhones and iPads, Android, and others, have essentially the same features.
It is turned on by default in all the operating systems when they are installed. Leave it turned on.
Make sure your operating systems Firewall is turned on.
Windows, Mac, and Linux all have Firewalls, parts of the operating system that intelligently choose what to let into the computer from the Internet. Usually, they only let replies in from Internet addresses that you set a request to.
Leave them turned on all the time.
Normally they won't give a home user any problems, but you may have to change some of the settings if you set up something such as home security cameras.
Windows: Start - Control Panel - System and Security - Windows Firewall - Turn Windows Firewall on or off
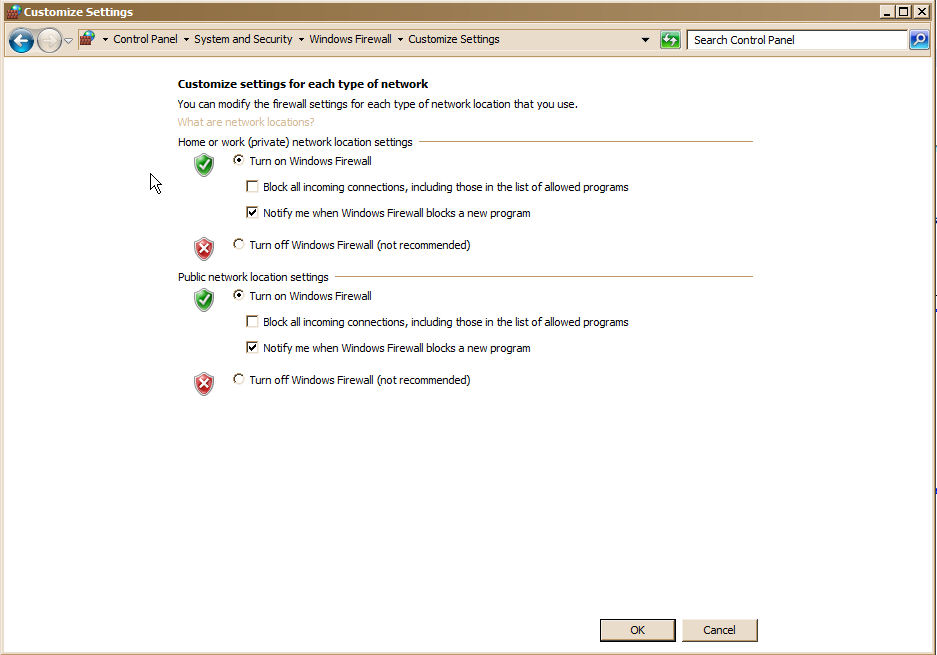
Mac: Apple symbol (upper left corner) - System Preferences - Security - Firewall and make sure Set access for specific service and applications is checked.
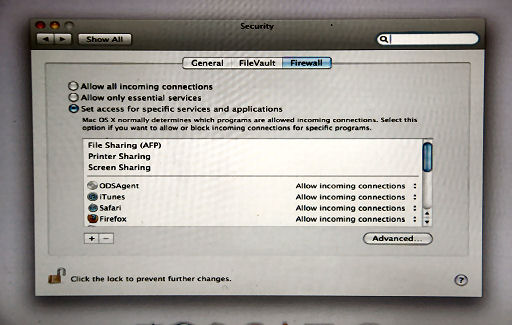
Never install a program unless it is from a trusted source, including programs on CD or flash drives, but especially from the Internet.
"User Account Control", on both Windows and the Mac, requires an administrative password to install a program. It's a pain, but don't turn it off. It will catch hidden or background installs from sources you may not know about.
Safe Surfing
Never click on an e-mail link, an e-mail attachment, or web page download unless you are sure it is a trusted source.
This is by far the most common source of Malware for home computer users.
Never open a Microsoft Office document (and many other documents for that matter) unless you know where they came from.
Usually data cannot install anything on your computer, but any program that has administrative rights can. If you open a document with a program that has administrative rights, the document may be able to ask the program to use those rights to alter your computer. It depends on the program. Microsoft Office is particularly vulnerable.
User Account Control will catch any such attempts and warn you.
Use "IPSec" (the little lock next to the address box, with an https:// before the address) whenever possible, especially when at a public Wi-Fi, such as Panera Bread or a motel.
Third Party Security Resources
Use a comprehensive Security Suite from a reputable manufacturer, such as Kaspersky, McAfee, or Norton.
Just a virus checker is not sufficient any more. There are too many other vulnerabilities than just viruses.
Here is a recent review from PC Magazine.
However, these Internet Security Suites can cause problems.
They can slow down your computer considerably.
Sometimes they can conflict with Windows firewall and cause strange problems. Follow the manufacturer's recommendations carefully.
If you are installing a major program on your computer, you may need to turn it off temporarily.
Although I don't necessarily recommend it, I don't use a Security Suite. I depend on my router, and Windows Firewall and the other security Windows provides.
Use a computer tracks cleaner regularly, if one is not included in your security suite.
I use CCleaner from Piriform.
Although from a profit making company, I have found it dependable and safe.
If you want to prevent anyone from tracking your browsing history, use Tor, from The Tor Project.
Available here: The Tor Project.
Open source, non-profit, and very dependable and secure
Sends all your web page requests through an encrypted link to Tor, which then forwards the request removing your return IP address, and sends the results back to you over the secure link.
The web sites you access only sees the request as one of very many from Tor, and therefore cannot identify any individual patterns or information in the requests.
Slows down your web browsing somewhat
Generalities
Generally, MacIntosh computers, Linux computers, tablets, iPads, and smart phones are much safer than PC's, but even they can be hacked.
They keep a lot tighter control over what programs are allowed to run than Windows does.
Using "Apps" on any computer, including Windows, is much safer than browsing the web.
This is true only if the App comes from a trusted source, such as the operating system "Store" or the specific company or institution, such as your bank, that supplies the App.
An "App" is just a regular computer program, but it has been verified by the supplier and communicates directly over the internet only to the originally intended destination.
Since it only does well defined tasks with only well defined web destinations, security is a lot easier to ensure.
Apps are quickly and automatically updated by the manufacturer if any security problems are found.
Any computer, such as an old Windows XP machine, that is not connected to the Internet is safe.
Use it as you always have. No one targets non-Internet computers any more.




